A modern, secure and future-proof cyber-secure system
Today, more than ever, businesses need security solutions that keep up with the changing pace of both the physical and digital world. Having the right systems in place allows you to ensure that the innovations needed to adapt quickly to the needs of the moment are available for the long term. Choosing the right security system will make it easy to work with in the future, because it can be complemented by innovation without changing the entire existing system - only adding the necessary tools to existing technical equipment when it is really needed. For example, managing CCTV, access control, security, number recognition, integrations with third-party applications all in one place.
It should also be noted that on 10 November 2023, the European Parliament approved the new NIS2 Directive, which aims to ensure a high level of cybersecurity throughout the European Union. The new Directive amends the rules on the security of networks and information systems with the aim of increasing the level of cyber resilience in all Member States.
How will the Regulation affect Latvian companies?
Increased cybersecurity requirements: new versions or amendments of cybersecurity directives usually introduce stricter or amended regulatory requirements. Businesses may face additional cyber security requirements to protect their networks and information systems. This may include implementing specific security measures, carrying out risk assessments and developing incident response plans.
Cybersecurity culture and training: to comply with the NIS, companies may need to promote a cybersecurity culture in their organisations. This includes training employees on cybersecurity best practices and integrating security measures into daily operations.
Four basic pillars
There are four pillars that are essential for a modern security system to comply with NIS2, which is what GENETEC has been working on for several years. Genetec is one of the industry's ambassadors in the construction and use of cyber security systems and is 100% NIS2 compliant.
E2EE End-to-end encryption is a secure communication method that prevents third parties from accessing data while it is being transferred from one end system or device to another. This solution ensures that the entire chain from the credentials to the server is fully encrypted/cybersecure.
APPLY FOR TRAINING ON STID AND GENETEC - 06.03.2024
Stronger risk and incident management and cooperation
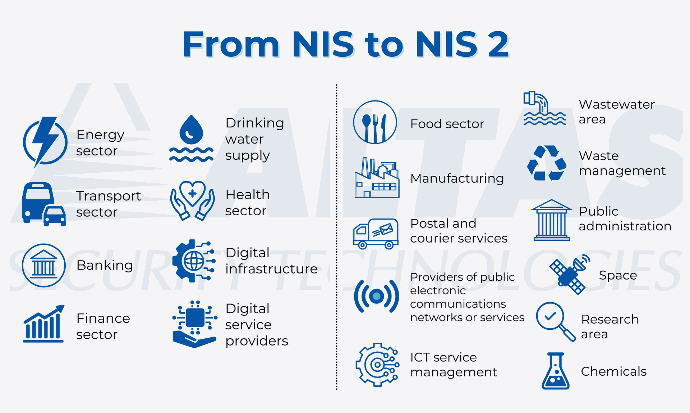
NIS2 will set the framework for cybersecurity risk management measures and reporting obligations in all sectors covered by the Directive, such as energy, transport, health and digital infrastructure.
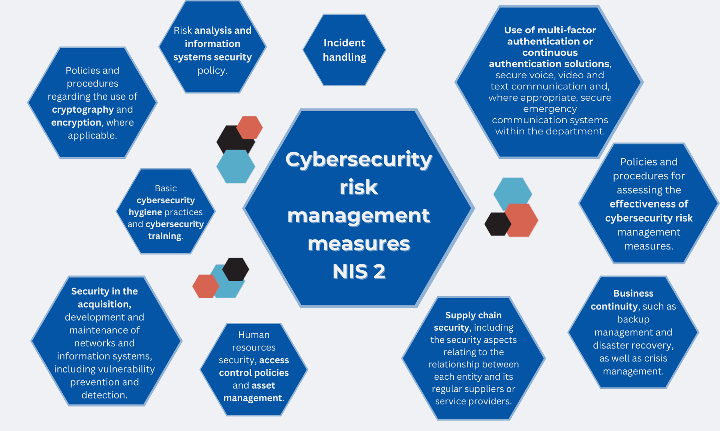
These measures are based on an "all-hazards approach" aimed at protecting network and information systems and their physical environment from incidents and include "at least" the following
Risk analysis and information systems security policy; Incident handling; Human resources security, access control policy and asset management.
Business continuity, such as backup management and disaster recovery, and crisis management.
Use of multi-factor authentication or continuous authentication solutions, secure voice, video and text communication and, where appropriate, secure emergency communication systems within the entity.
Supply chain security, including security aspects relating to the relationship between each entity and its direct suppliers or service providers.
Security for the acquisition, development and maintenance of networks and information systems, including vulnerability handling and disclosure.
Policies and procedures for assessing the effectiveness of cybersecurity risk management measures.
Basic cyber hygiene practices and cyber security training.
Policies and procedures regarding the use of cryptography and, where appropriate, encryption.
Comments Roberts Jansons, Sales Manager at STid: "So, in order to mitigate potential threats from neighbouring countries close to us, especially Latvia, network information security laws were introduced. The first ones came in 2016 - NIS1.

New laws were established last year and started to be implemented in January this year. How will this affect us? To be honest, everyone has different thoughts on this - some are worried about the potential problems that this regulation may cause them, others about whether they will cope with the mandatory obligations, whether it applies to them as a company at all and how the employees in a particular company will be affected? How will the national agencies implement these directives in national law? Who will be able to support in the eventual implementation of this regulation and when should be ready if the regulation is applied.
When the GDPR came into force in 2018, 25 May was a sacred date for all countries, because this date was the key to everything. Not so with NIS2. It needs to be implemented in international law in all EU countries. This must be done by 17 October next year. To simplify the explanation, this is about comprehensive safety, to make sure that we protect ourselves, our communities, our children and the elderly, our lung and heart support equipment, as well as diabetic equipment, which are pacemakers. This applies to absolutely everything at the same time across Europe to make sure that we are safe. And this is not about games or other things in our pockets.
NIS1 was more about logical security, i.e. IT systems. NIS2 also introduces physical security requirements, including end-to-end physical security. International cooperation between countries is also very important here. This is all managed by ENISA (the European Union Agency for Cyber Security), which has a national organisation in each EU country that can be contacted on any issue related to the implementation of NIS2.
Now, with NIS2, we will see virtually everyone who has anything to do with maintaining society - from food logistics to credit unions. In other words, everyone is included in this exercise."
APPLY FOR NORDIC SECTECH SUMMIT 2024 - October 17th, 2024
Anna Vladimirova-Kryukova from Cobalt Latvia: "This regulation is not just a public enforcement decision, it is also a motivation for business to do something to ensure compliance. Because somewhere in another part of this chain, someone will probably be prosecuted in a regulatory context with a law enforcement context. And then you will have to be compliant because it happens all along the chain.
This can be both short-term and long-term motivation. If you are in business or want to survive in your industry for longer, your business partners will eventually demand that you meet these requirements. Regulators are also likely to demand it. This is influenced by the political situation, business requirements and the introduction of new technologies - all in all, a lot of pressure is expected. NIS2 is leading the way in this respect. This Regulation applies to different types of market players - products and service providers with digital elements. The scope is therefore broad and addresses cybersecurity not only in the production process, but right from the product and service architecture planning stage, through production, export, import and sale to customers. So basically it touches the whole product life cycle."
Whereas under the previous NIS Directive Member States were responsible for determining which entities met the criteria to qualify as essential service providers, the new NIS Directive introduces a size limitation rule. This means that the Directive will apply to all medium and large companies operating in the sectors or providing the services covered by the Directive.
What this level of security means. If we look at what is happening in Latvia at the moment, for example, we have a very popular Cabinet Decision No 442, which requires specific security measures to be taken, mainly in the public sector, but also for digital and some utility providers. But when the scope is broader, the concept, at least in Latvia, will be quite similar to NIS2 - a very specific list of security requirements," says Vladimirova-Kryukova. For more on Cobalt's senior associate's experience and vision, as well as the relationship between NIS2 and the Digital Operating Resilience Act (DORA) here.
Sanctions
The NIS2 has established a broader set of powers to be granted to competent authorities. In addition, the governance bodies will play a significant and active role in the monitoring and implementation of these measures. What is the risk if the cybersecurity measures implemented by a company do not meet the requirements?
Fines of up to EUR 10 million or 2% of total annual turnover
Direct management responsibility (CISOs, heads of IT and C-level executives)
Temporary bans on managers working in managerial positions
Appointment of the Supervisory Officer
Oskars Pirags, ALTAS IT Business Development Director: "Each Member State will have 21 months to incorporate the provisions of the Directive into their legislation as well as to implement it. Basically, it is envisaged that critical sector infrastructure must be protected accordingly, not just on a voluntary basis, but on a mandatory basis. For example, an acceptable level of access control is if there is an installation where the keys are in the reader. In order to communicate with the cards, the reader must store the keys in an EAL5+ container, which is automatically deleted in the event of the card reader's security switch being tripped. The EAL5+ level is mandatory for all parts, starting from the storage of credentials, the communication of credentials with the reader, and the communication of readers with controllers."
To make it easier to prepare, there is a need to create a voluntary, mutually agreed mechanism that will foster mutual trust and learning from best practices and experiences, thus contributing to achieving a high common level of cyber security. By sharing our experiences, receiving feedback from the responsible authorities and providing training workshops for our staff, the implementation and handling of the Directive will become easier.
APPLY FOR NORDIC SECTECH SUMMIT 2024 - October 17th, 2024
Source: https://www.nis-2-directive.com/
https://www.nomios.com/news-blog/nis2-advice-ciso/
https://youtu.be/PYEcs07RgoA?list=UULFce9Nj37oCTibpJ1btws79
https://youtu.be/oI0xElTwWyE?list=UULFce9Nj37oCTibpJ1btws79Q
https://utimaco.com/compliance/compliance-and-standardization/nis2-directive-compliance